System Information Leak Internal Fortify

5 simple tips to know if a website is safe or fake.
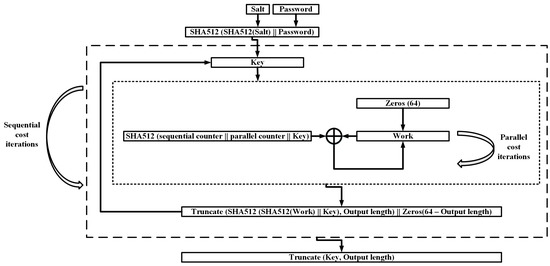
System information leak internal fortify. About micro focus fortify software security research. Top cybersecurity trends in 2020. An external information leak occurs when system data or debugging information leaves the program to a remote machine via a socket or network connection. For each issue addressed via code changes or documented on the wiki as a non issue mitigable.
Ensure that error codes and other messages visible by end users do not contain sensitive information. Internal system information leak severity. See the fortify connect spreadsheet for individual findings and appendix f for detailed explanations recommendations. A description language and tooling for hypermedia driven restful apis restful api description language radl.
The application calls methods of the log class. Address system information leak fortify scan results. Unlike traditional network security fortify sca. The fortify software security research team translates cutting edge research into security intelligence that powers the fortify product portfolio including fortify static code analyzer sca fortify webinspect and fortify application defender.
An external information leak occurs when system data or debugging information leaves the program to a remote machine via a socket or network connection. Internal system information leak. Leakage of system data or debugging information through an output stream or logging function can allow attackers to gain knowledge about the application and craft specialized attacks on the it. Cordova android 5 2 2 and below description.
External leaks can help an attacker by revealing specific data about operating systems full pathnames the existence of usernames or locations of configuration files and are more serious than internal information leaks which are more difficult for an attacker to access. The fortify sca tool attempts to protect systems from security flaws in business critical software applications. For each issue addressed via code changes or documented on the wiki as a non issue mitigable. Prevent ehr hacking patient data breach with the 3 way approach in 2020.
The apache software foundation versions affected. The information revealed by println could help an adversary form a plan of attack. See the fortify connect spreadsheet for individual findings and appendix f for detailed explanations recommendations. Tue 9 may 2017 14 49 56 0100.



:background_color(FFFFFF):format(jpeg)/images/library/11117/arteries-and-veins-of-cardiovascular-system_english.jpg)